Network Security Toolkit on:
[Wikipedia]
[Google]
[Amazon]
Network Security Toolkit (NST) is a
 The following image depicts the ''interactive'' dynamic SVG/
The following image depicts the ''interactive'' dynamic SVG/
NST at SourceForge
{{Linux distributions Operating system distributions bootable from read-only media Linux security software Network analyzers Free network management software Remote desktop Computer security software Unix network-related software
Linux
Linux ( or ) is a family of open-source Unix-like operating systems based on the Linux kernel, an operating system kernel first released on September 17, 1991, by Linus Torvalds. Linux is typically packaged as a Linux distribution, which ...
-based Live DVD
The DVD (common abbreviation for Digital Video Disc or Digital Versatile Disc) is a digital optical disc data storage format. It was invented and developed in 1995 and first released on November 1, 1996, in Japan. The medium can store any kin ...
/USB Flash Drive
A USB flash drive (also called a thumb drive) is a data storage device that includes flash memory with an integrated USB interface. It is typically removable, rewritable and much smaller than an optical disc. Most weigh less than . Since firs ...
that provides a set of free and open-source
Free and open-source software (FOSS) is a term used to refer to groups of software consisting of both free software and open-source software where anyone is freely licensed to use, copy, study, and change the software in any way, and the source ...
computer security
Computer security, cybersecurity (cyber security), or information technology security (IT security) is the protection of computer systems and networks from attack by malicious actors that may result in unauthorized information disclosure, the ...
and networking tools to perform routine security and networking diagnostic and monitoring tasks. The distribution can be used as a network security analysis, validation and monitoring tool on servers hosting virtual machines
In computing, a virtual machine (VM) is the virtualization/emulation of a computer system. Virtual machines are based on computer architectures and provide functionality of a physical computer. Their implementations may involve specialized hardw ...
. The majority of tools published in the article "Top 125 security tools" by Insecure.org are available in the toolkit. NST has package management capabilities similar to Fedora
A fedora () is a hat with a soft brim and indented crown.Kilgour, Ruth Edwards (1958). ''A Pageant of Hats Ancient and Modern''. R. M. McBride Company. It is typically creased lengthwise down the crown and "pinched" near the front on both sides ...
and maintains its own repository of additional packages.
Features
Many tasks that can be performed within NST are available through aweb interface
In the industrial design field of human–computer interaction, a user interface (UI) is the space where interactions between humans and machines occur. The goal of this interaction is to allow effective operation and control of the machine fr ...
called NST WUI. Among the tools that can be used through this interface are nmap
Nmap (Network Mapper) is a network scanner created by Gordon Lyon (also known by his pseudonym ''Fyodor Vaskovich''). Nmap is used to discover hosts and services on a computer network by sending packets and analyzing the responses.
Nmap provides ...
with the vizualization tool ZenMap, ntop
ntop is computer software that probes a computer network to show network use in a way similar to what the program top does for processes.
Software
In interactive mode, it displays the network status on the user's terminal. In Web mode, it act ...
, a Network Interface Bandwidth Monitor, a Network Segment ARP Scanner, a session manager for VNC
Virtual Network Computing (VNC) is a graphical desktop-sharing system that uses the Remote Frame Buffer protocol (RFB) to remotely control another computer. It transmits the keyboard and mouse input from one computer to another, relaying the g ...
, a minicom
Minicom is a text-based modem control and terminal emulator program for Unix-like operating systems, originally written by Miquel van Smoorenburg, and modeled somewhat after the popular MS-DOS program Telix but is open source. Minicom includ ...
-based terminal server, serial port
In computing, a serial port is a serial communication interface through which information transfers in or out sequentially one bit at a time. This is in contrast to a parallel port, which communicates multiple bits simultaneously in parallel. ...
monitoring, and WPA
WPA may refer to:
Computing
*Wi-Fi Protected Access, a wireless encryption standard
*Windows Product Activation, in Microsoft software licensing
* Wireless Public Alerting (Alert Ready), emergency alerts over LTE in Canada
* Windows Performance An ...
PSK management.
Other features include visualization of ntopng
ntopng is computer software for monitoring traffic on a computer network. It is designed to be a high-performance, low-resource replacement for ntop. The name is derived from ''ntop next generation''. ntopng is open-source software released u ...
, ntop
ntop is computer software that probes a computer network to show network use in a way similar to what the program top does for processes.
Software
In interactive mode, it displays the network status on the user's terminal. In Web mode, it act ...
, wireshark
Wireshark is a free and open-source packet analyzer. It is used for network troubleshooting, analysis, software and communications protocol development, and education. Originally named Ethereal, the project was renamed Wireshark in May 2006 d ...
, traceroute
In computing, traceroute and tracert are computer network diagnostic commands for displaying possible routes (paths) and measuring transit delays of packets across an Internet Protocol (IP) network. The history of the route is recorded as th ...
, NetFlow
NetFlow is a feature that was introduced on Cisco routers around 1996 that provides the ability to collect IP network traffic as it enters or exits an interface. By analyzing the data provided by NetFlow, a network administrator can determine thin ...
and kismet data by geolocating the host addresses, IPv4 Address conversation, traceroute
In computing, traceroute and tracert are computer network diagnostic commands for displaying possible routes (paths) and measuring transit delays of packets across an Internet Protocol (IP) network. The history of the route is recorded as th ...
data and wireless access point
In computer networking, a wireless access point (WAP), or more generally just access point (AP), is a networking hardware device that allows other Wi-Fi devices to connect to a wired network. As a standalone device, the AP may have a wired co ...
s and displaying them via Google Earth
Google Earth is a computer program that renders a 3D computer graphics, 3D representation of Earth based primarily on satellite imagery. The program maps the Earth by superimposition, superimposing satellite images, aerial photography, and geog ...
or a Mercator World Map __NOTOC__
Mercator (Latin for " merchant") may refer to:
People
* Marius Mercator (c. 390–451), a Catholic ecclesiastical writer
* Arnold Mercator, a 16th-century cartographer
* Gerardus Mercator, a 16th-century cartographer
** Mercator 156 ...
bit image, a browser-based packet capture and protocol analysis system capable of monitoring up to four network interfaces using Wireshark
Wireshark is a free and open-source packet analyzer. It is used for network troubleshooting, analysis, software and communications protocol development, and education. Originally named Ethereal, the project was renamed Wireshark in May 2006 d ...
, as well as a Snort-based intrusion detection system
An intrusion detection system (IDS; also intrusion prevention system or IPS) is a device or software application that monitors a network or systems for malicious activity or policy violations. Any intrusion activity or violation is typically rep ...
with a "collector" backend that stores incidents in a MySQL
MySQL () is an open-source relational database management system (RDBMS). Its name is a combination of "My", the name of co-founder Michael Widenius's daughter My, and "SQL", the acronym for Structured Query Language. A relational database o ...
database. For web developers, there is also a JavaScript
JavaScript (), often abbreviated as JS, is a programming language that is one of the core technologies of the World Wide Web, alongside HTML and CSS. As of 2022, 98% of Website, websites use JavaScript on the Client (computing), client side ...
console with a built-in object library
In computer science, a library is a collection of non-volatile resources used by computer programs, often for software development. These may include configuration data, documentation, help data, message templates, pre-written code and subro ...
with functions that aid the development of dynamic web page
A server-side dynamic web page is a web page whose construction is controlled by an application server processing server-side scripts. In server-side scripting, parameters determine how the assembly of every new web page proceeds, and includin ...
s.
Host Geolocations
The following examplentop
ntop is computer software that probes a computer network to show network use in a way similar to what the program top does for processes.
Software
In interactive mode, it displays the network status on the user's terminal. In Web mode, it act ...
host geolocation images were generated by NST.
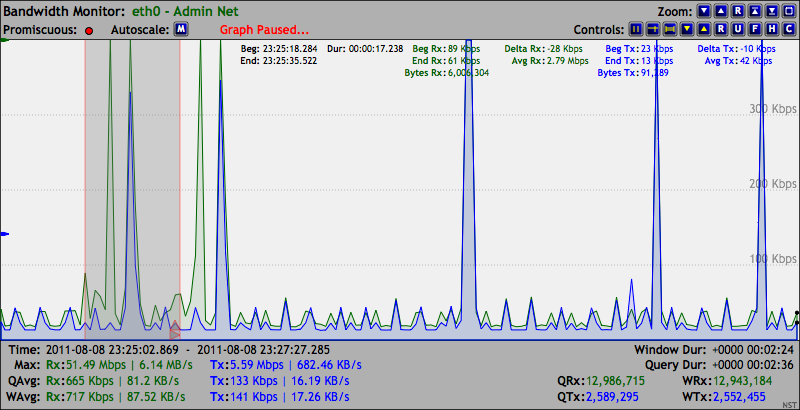
Network Monitors
 The following image depicts the ''interactive'' dynamic SVG/
The following image depicts the ''interactive'' dynamic SVG/AJAX
Ajax may refer to:
Greek mythology and tragedy
* Ajax the Great, a Greek mythological hero, son of King Telamon and Periboea
* Ajax the Lesser, a Greek mythological hero, son of Oileus, the king of Locris
* ''Ajax'' (play), by the ancient Greek ...
enabled Network Interface Bandwidth Monitor which is integrated into the NST WUI. Also shown is a Ruler Measurement tool overlay to perform time and bandwidth rate analysis.
See also
*BackTrack
BackTrack was a Linux distribution that focused on security, based on the Knoppix Linux distribution aimed at digital forensics and penetration testing use. In March 2013, the Offensive Security team rebuilt BackTrack around the Debian distr ...
*Kali Linux
Kali Linux is a Debian-derived Linux distribution designed for digital forensics and penetration testing. It is maintained and funded by Offensive Security.
Kali Linux has around 600 penetration-testing programs (tools), including Armitage (a gr ...
* List of digital forensic tools
During the 1980s, most digital forensics, digital forensic investigations consisted of "live analysis", examining digital media directly using non-specialist tools. In the 1990s, several freeware and other proprietary tools (both hardware and softw ...
*Computer Security
Computer security, cybersecurity (cyber security), or information technology security (IT security) is the protection of computer systems and networks from attack by malicious actors that may result in unauthorized information disclosure, the ...
*List of live CDs
This is a list of live CDs. A live CD or live DVD is a CD-ROM or DVD-ROM containing a bootable computer operating system. Live CDs are unique in that they have the ability to run a complete, modern operating system on a computer lacking mutable ...
References
External links
*NST at SourceForge
{{Linux distributions Operating system distributions bootable from read-only media Linux security software Network analyzers Free network management software Remote desktop Computer security software Unix network-related software